Bunkerkit is a fully modular concept for the cumulative physical protection of data centers and data rooms against various threats.
We install armored data centers whose walls, floors, ceilings, doors and windows are equipped with the following cumulative properties:
EMC Shielding: The entire data room is a large Faraday cage to protect the hardware against EMP and EMI with attenuation values of up to 100 dB over a frequency range between 9 kHz and 18 kHz, in accordance with standard EN 299-2006.
The Bunkerkit data center is also TEMPEST certified and therefore meets the standards to prevent data theft and data compromise by capturing electromagnetic signals emitted by the data center.
Burglar-resistant: the walls (WK2 to WK6), the doors (WK2 to WK6) and the windows (WK2 to WK5) are burglar-resistant in accordance with the EN 1627-1630 standard.
Bulletproof: especially for data centers containing sensitive data that could be the target of terrorist attacks or criminal activities, they are provided with bulletproof properties in accordance with class FB4 to FB7 according to standard EN 1522-1523.
Fire-resistant: for good fire compartmentalization, both in the event of a fire in the data center and outside, the walls, doors and windows are made fire-resistant in accordance with the standards, depending on the desired level of protection.
After all, a data center can be exposed to numerous threats. Some threats, such as a thermonuclear nuclear explosion are hopefully not directly relevant, but burglary, vandalism, fire and problems with electromagnetic disturbances are threats that must be taken seriously on a daily basis.
Potential threats to data rooms and data centers
Espionage and Hacking
Professional data centers are now seriously protected against malware infiltration by sophisticated hardware and software firewalls and malware scanners.
But, although it seems like something out of a science fiction movie, it is indeed possible with advanced equipment to ‘read’ the electromagnetic signals that are inevitably emitted by cables and computers. By converting these signals back into data, sensitive data can be obtained in this way. It is not necessary to have physical access to the data center for this. The data can also be read using a drone with a very small chance of detection. That is why the Bunkerkit is TEMPEST certified to provide a solid response to these types of threats.
EMP (Electromagnetic Pulse)
Another threat to data centers and data rooms are EMPs or Electromagnetic Pulses. An EMP is capable of severely damaging the data on servers in a data center. You can compare it with a strong electromagnet that moves you over a hard disk. There is a very good chance that the data on that hard drive is irretrievably lost.
There are three major sources of EMPs:
Electromagnetic pulses from solar storms
In July 2012, Earth’s egg was almost catapulted back to the Stone Age by the largest electromagnetic pulse ever seen from a giant solar storm. The pulse missed Earth by a hair. Solar storms occur regularly and the increase in electromagnetic radiation that accompanies them is definitely something to take into account when setting up an EMC-safe data center.
Fortunately, we have only been hit by one major storm in modern times, which caused the 1989 Quebec power outage.
Impact from a thermonuclear attack
The EMP is a notorious phenomenon that is feared by governments. After the nuclear explosions in Nagasaki and Hiroshima, all electrical equipment failed miles away due to the gamma radiation released. In our digitized society, such a blackout would cause even more (economic) damage than the nuclear explosion itself.
Various nuclear powers have EMP weapons that literally fry all electronic equipment within a radius of hundreds of kilometers from the target.
Now we all hope that the great powers on Earth use their common sense, but nuclear weapons are there and even with targeted use on a limited scale, it is a real threat that should be taken into account immediately when setting up a data center .
Terrorism
One form of terrorism we may encounter is the use of a home-made EMP generator. Making such a life-threatening EMP weapon is within reach of anyone who has some knowledge of electronics and can put together a strong electromagnet. The EMP generator can release a large amount of electromagnetic energy in a short time. When terrorists manage to penetrate a data center with such an EMP generator, serious to irreparable damage can be caused to the data storage.
EMI (Electromagnetic Interference)
Unlike EMP, Electromagnetic Interference is more of a technical nature, inherent to the use of electronics and the transmission of data signals. After all, this causes various kinds of disturbances due to the electromagnetic fields and signals generated by the electronic components in computers. The signals and energy that are transported in data cables and power cables are also formidable sources of interference.
But EMI works both ways. Equipment and machines located near computers can interfere with the operation of the computers. Just think of a mobile phone that causes interference on speakers. On the other hand, the electromagnetic radiation from the data center itself can also cause unwanted interference to other equipment inside and outside the data center.
The list of equipment that can be a source of failure for the data center is quite impressive. Radio transmitters, TV, radio amateurs, radars, satellite telephones and mobile phones, industrial, scientific and medical equipment, microprocessors (because of their high clock speed), power converters and power generators, light dimmers, welding equipment, starting electric motors, all kinds of relays, transformers, … are all potential hazards for malfunctions on the cabling and hardware (firewalls, servers, …) within the data center.
Security of the data center against burglary
It goes without saying that the data rooms of a data center are properly secured against unauthorized access and break-ins.
For data centers for military applications, governments, the banking sector and other institutions where very sensitive data is stored, it is even recommended to go for maximum security and not only to provide burglar-resistant doors and windows, but also to provide them with bullet-resistant and fire-resistant characteristics.
Protection of the data center against fire
Fire-resistant doors, windows and walls prove their usefulness in two directions in a data center. When a fire breaks out elsewhere in the building, protecting the data center and servers is just as important as protecting the staff.
But when a fire breaks out in the data center, it is at least as important that the rest of the building can be preserved and that staff can get to safety in time. A data center also contains hardware equipped with lithium-ion batteries (e.g. UPS uninterruptible power supplies), which cause violent combustion, releasing toxic gases. These types of fires are very difficult to extinguish. In that case, good fire compartmentalisation can save lives and shield the rest of the building.
Bunkerkit: the best physical protection for your data center
Bunkerkit is the solution of choice for the physical protection of your data center and is able to cope with any of the listed threats.
Only with EMI (Electromagnetic Interference) is there a shared responsibility, on the one hand, for the physical shell of the data center and the cable transits and, on the other hand, for the types of cabling used, the design and grounding of the server park and the network cabling.
For the other threats mentioned, the solution lies in the design of the walls, floors, ceilings, windows, doors and cable ducts. Bunkerkit is the ideal solution for countering these threats.
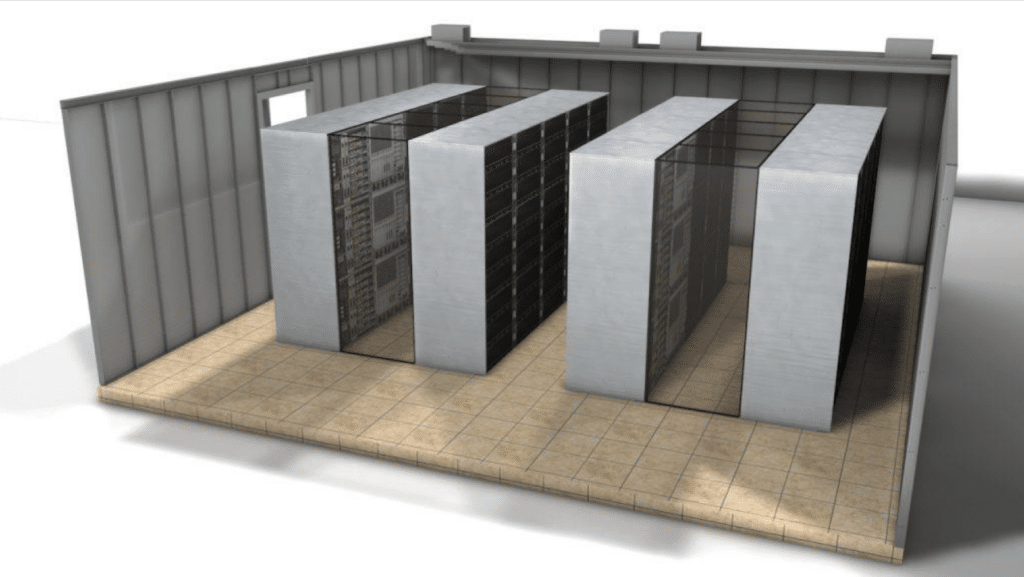
The Bunkerkit Data Center can be executed in various sizes, ranging from a modest data room for one or a few servers and peripherals, to real data centers for large companies, banks, telecom companies, hosting companies, social media companies, military data centers and data centers of government institutions.

Small application of Bunkerkit as a data room for only a few computers and peripherals.

Since we work with armored steel profiles and walls that are screwed together, there is no limit to the size of the shell in which the data center is housed and large, complex constructions are also possible.
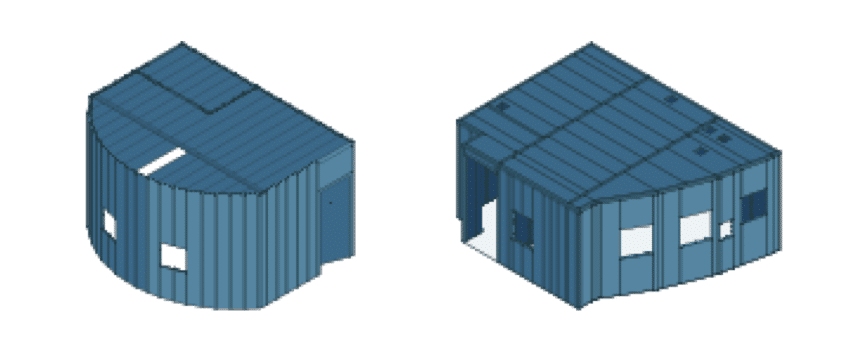
The shape of the Bunkerkit does not have to be limited to a square or rectangular structure. More complex shapes and semicircular walls are also possible.
Properties of Bunkerkit data centers
EMC shielding (Faraday cage)
The walls, floor, ceiling and even the windows together form a large Faraday cage. They can be realized in different sizes with very high attenuation values, up to 100 dB in a frequency range from 9 kHz to 18 GHz.
They have very specific specifications and are normally used to certify or qualify electronic products. The entire structure is realized in metal panels with shielded gaskets in between.
The doors are also realized very accurately. For example, they have locking mechanisms, with or without access control. Metal leaf contacts and gaskets maintain the Faraday cage to ensure proper EMC shielding.
Interconnections are filtered for both the main electrical lines and the interconnected parts of equipment, while shielding filters are used that are appropriate for the type of signal required.
The modular structure provides remarkable construction flexibility, enabling any technical requirement to be met.
Bunkerkit also offers an alternative solution by working with a conductive substance. This type of shielding is offered as a solution for more modest requirements, but is still valid as an answer to market demand. This budget-friendly method guarantees a decrease of 50-60 dB over a frequency range between 9 KHz and 18 GHz by coating all structures of the walls (including curved ones) with the protective fabric.
Conductive gaskets
The conductive gaskets are built up on the basis of various concentric metal chain mail. The standard material used is Cupro (a nickel-copper alloy). However, the material used is determined by the degree of protection required.
Filters on the cable entries
Depending on the type of power cable, different types of filters must be installed. These are necessary to prevent electromagnetic disturbances on the data center’s connections to the outside world.
Honeycomb filters
Honeycomb filters are used to provide effective electromagnetic shielding while ensuring excellent airflow. The filters can be supplied in different materials, with or without EMI/EMC frame and gaskets.
Windows
Glass surfaces are a serious challenge to ensure EMC shielding. In order to be able to close and respect the Faraday cage concept in the data center, with a good compromise between visibility and the required shielding value, we use armored windows in tempered glass or thermoplastic material. These can be made in different thicknesses, transparent or colored.
A gauze with the desired opening degree of 80 to 130 mesh is processed in the window using an autoclave. Depending on the degree of protection required, this mesh in metal wire or polyester or polyamide treated with copper or nickel is used.
Fire-resistant, burglary-resistant and bullet-resistant
Depending on the requirements and the threat level, the entire data center can be made fire-resistant (fire-resistant class according to need), burglary-resistant (class WK2 to WK6 ) and bullet-resistant (class FB4 to FB7).
Burglar-resistant ventilation grilles
We also pay a lot of attention to securing ventilation openings using burglary-resistant ventilation grilles developed by us with a resistance class wk3, wk4 or wk5.

Finish
Depending on the application, the walls of the Bunkerkit can be left visible or finished with an inner or outer cladding of your choice.
The ceiling and floor can also be finished so that ventilation and lighting can be integrated into the ceiling as desired.

Frequently Asked Questions about Bunkerkit Data Center
Bunkerkit supplies advanced modular panels for the protection of critical infrastructure, such as data centers and IT rooms. They offer solutions that protect against various threats such as EMC, burglary, fire, bullets and explosions.
Bunkerkit offers different levels of security based on the specific needs of the customer. This can range from basic protection to advanced protection against multiple threats. Burglary resistant: from WK2 to WK6. Fire resistant: all common levels, depending on your requirements. Bulletproof: from FB4 to FB7. EMC: up to 100 dB over a frequency range between 9 kHz and 18 GHz.
Bunkerkit’s modular panels are designed to withstand physical threats such as burglary attempts, bullets and explosions. They also provide protection against technical threats, such as fire and electromagnetic radiation, by using specialized materials and techniques.
Some of the benefits of using Bunkerkit’s modular panels are: quick and easy installation, adaptability to different spaces and configurations, high level of security and protection, and the ability to upgrade or expand security in the future.
When moving, the data center can be dismantled and rebuilt at the new location.
Yes, Bunkerkit can provide custom solutions based on your specific needs and requirements. We work closely with customers to develop a solution that meets their unique security needs. You can choose which burglary-resistant and bullet-resistant class is required and which fire-resistant specifications your data center must meet. Different levels can also be provided for the EMC shielding. You can also choose from various sizes, shapes and interior and exterior finishes.
Installation time may vary depending on the size and complexity of the project. However, Bunkerkit’s modular panels are designed for quick and easy installation, often reducing installation time compared to traditional construction methods.
Bunkerkit’s modular panels can be easily integrated into existing buildings and IT infrastructures. They are designed to adapt to different spaces and configurations, making them suitable for both new builds and renovation projects.
The cost of implementing a Bunkerkit data center varies depending on the specific needs and requirements of your project. Factors that affect costs include the level of security, the size and complexity of the project, and the modifications required. For an accurate quote, it is recommended that you contact Bunkerkit and discuss your specific needs. Our experienced experts will prepare a tailor-made offer according to your needs.
Given the often very confidential nature of securing data centers, we cannot go into detail about our customers and the various case studies. We can reveal that we have set up various data centers worldwide for military and government institutions and for various well-known telecom operators and banks. Numerous private companies also use our products to set up and protect everything from small IT premises to large data centers, including Google and Telenet.

